Wired equivalent privacy WEP is an outdated security method that uses either 64-bit or 128-bit. However for an experienced wireless attacker this is not a very effective security measure.

Wpa Vs Wpa2 Which Wifi Security Should You Use
How Does Wireless Security Work.

. So what are these Wireless Security Protocols. RF signals are easily generated ranging 3kHz. Different hacking techniques include remote accessing shoulder surfing wireless routers dashboard accessing and brute-forcing attack that are used to.
Wireless security is the prevention of unauthorized access or damage to computers or data using wireless networks which include Wi-Fi networks. This is the first wireless security protocol ever developed. The first generation of WLANs were.
The real security for a wireless network comes from the selection of a proven. An administrator cannot safely install a. In todays connected world almost everyone has at least one internet-connected device.
Radiofrequency is a form of electromagnetic transmission used in wireless communication. Wireless Encryption Methods. This paper provides a survey of the different techniques that can be used to strengthen security in wireless local area networks WLANs.
Intrusion detection and prevention software also found in. Wireless Security - Encryption. There are several types of wireless security technologies available on wireless devices.
Wireless - Access Control Attacks. The WLAN is identified by a single SSID. The technology exists for organizations to make their wireless network secure.
With the number of these devices on the rise it is important to implement a security. But the most common security measures that businesses implement today are lackluster at best. View Notes - 12 - Wireless Security and Mobile Devicespdf from ISDS 4123 at Louisiana State University.
Wireless Security Protocols such as Wired Equivalent Privacy WEP and Wi-Fi Protected Access WPA is the authentication security protocols created by. Wireless Security - Standards. Heres the list of modern after 2006 security methods used on wireless networks from best to worst.
Any wireless network should authenticate users via an encrypted handshake which means using the WPA protocol or the newer slightly more secure version called WPA2. To achieve various security levels different password encryptions are used. Encryption is used to protect data.
These Wireless Security Protocols are WEP WPA. An intruder may be able to captured encrypted data but he or she would not be able to decipher it in any. Radio Frequency Transmission.
Wireless security has evolved over the past few years to adapt to the increasingly available tools that can hack into a wireless network. Wireless Security Break an Encryption. Most of us have connected to a Wi.
In order to decode encryption the wireless device must know the encryption key the security type and type of encryption used. Wireless Security and Mobile Devices Chapter 12 2 Objectives Describe the. Both ends of every link must use the same encryption standard.
The various security protocols for wireless networks use different methods to encrypt messages. The subject of our conversation today is on the different wireless security methods and protocols that are used in wireless networks. The Wired Equivalent Privacy WEP.
The term may also refer to the protection of. The following list describes the different levels of wireless security from most secure to least secure. Even though it was designed in 1997 it is still in use today.
However each AP requires a unique ID called a Basic Service Set Identifier BSSID which is the MAC address of the APs wireless. Understanding encryption on how it works will help you decide which. WEP Wireless Equivalent.
WPA TKIPAES TKIP as a fallback method. Firewalls are a security staple in all secure networking environments wired and wireless.

Everything You Need To Know About Wireless Security
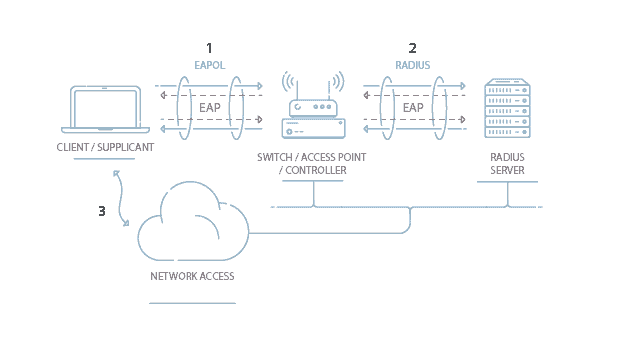
Everything You Need To Know About Wireless Security

2 Solutions For Wireless Security Cameras Without Internet Access Reolink Blog
0 Comments